 Elderly Americans lost $12.5 billion in 2024 according to the numbers released by the Federal Trade Commission. This is up from 2023's $10 billion lost to scammers by elderly Americans. And that number is astronomically higher than 2020's $3.5 billion lost by elderly Americans. There are two questions that need to be asked: 1. What can be done to prevent these scams? 2. What can you, as friends and family, do help after someone has fallen victim to a scam?
Elderly Americans lost $12.5 billion in 2024 according to the numbers released by the Federal Trade Commission. This is up from 2023's $10 billion lost to scammers by elderly Americans. And that number is astronomically higher than 2020's $3.5 billion lost by elderly Americans. There are two questions that need to be asked: 1. What can be done to prevent these scams? 2. What can you, as friends and family, do help after someone has fallen victim to a scam?
How to Prevent Scams
Prevention is the goal, but scammers are professional social engineers so if they successfully make contact with an elderly person chances are they will have a way to get them to do what they want. So true prevention can only be accomplished by completely removing potential access between the scammers and potential victims. And to that end I can't imagine someone wanting giving up their Internet, cell phones or even home phones for those that still have a home phone line, but that would be the only way to truly prevent any access from these types of scammers.
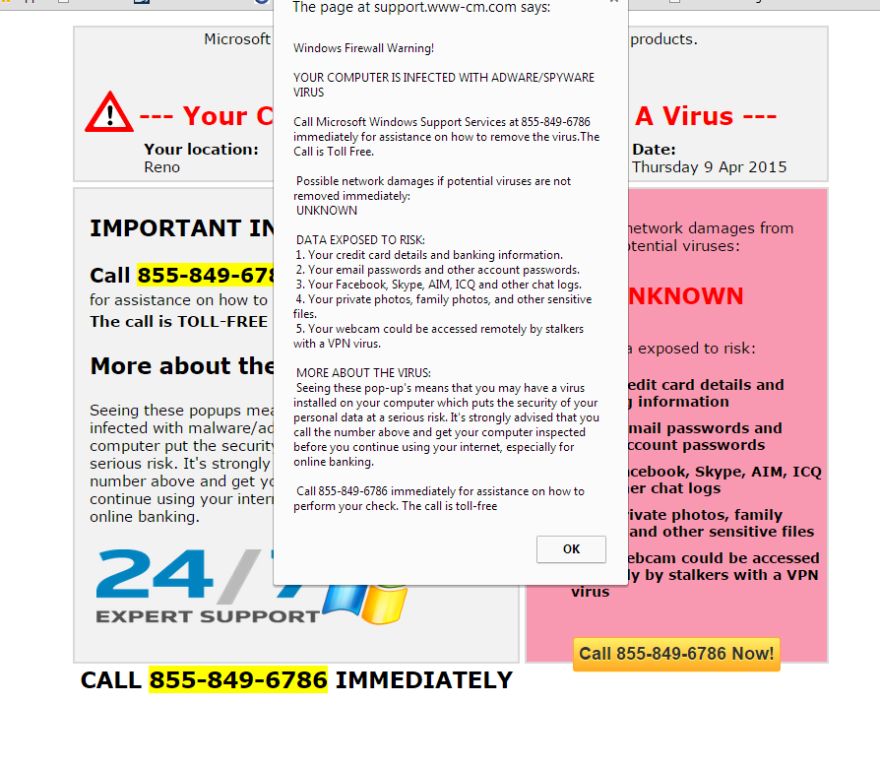
So then what's Plan B? Remarkedly like our parents told us over and over when we were kids, we now need to remind them over and over again to never call a phone number that pops up on your computer, never allow anyone to access your computer remotely (I used to say unless you know them or can walk into the company's office and meet the staff, but more and more scammers are pretending to be those local companies so I can no longer provide this exception), and do not answer calls from unknown numbers.
Once the scammers have the elderly on the phone they have a repertoire of ways to bend the victim to their will. The first way the scammer has to get the elderly to be compliant is care and compassion. "Oh yes it's good you called, that popup means your computer is badly infected. Give me access to your computer and I'll help you." OMG he's so nice he's going to get this horrible virus off my computer... but in reality he's going to steal your credentials, get into your bank accounts, and try and bleed you dry. If care and compassion aren't working they usually go next to fear. "Oh if you don't let me on your computer we can't stop the bad people from using that virus to steal all of your money." Don't you mean you need on my computer so you can be the bad guy to do that? Fear of financial loss is very effective to convince the elderly to be compliant.
Another frequent scam right now is the fake Paypal / eBay / iTunes / etc invoice. There's always a number to call to get that straightened out and that call will take you to someone very "helpful". A person who for some bizarre reason needs access remotely to your computer, but ok he's helping...right? Wrong! In this scam you will be asked to log into your bank account while he's on the computer with you...only he will be stealing your banking credentials (and any other credentials he can, especially your email so he can cut you off from seeing all the things he's about to do). Then in a long story short he will "accidentally" refund you too much money and so he doesn't get fired now you have to get gift cards or Bitcoin or something to get the extra money back to him so he's not fired. He's so scared of being fired!!! And you wouldn't want his "innocent" mistake to cost him his job, would you?
Usually it goes down like this, he's now showing you completely fake banking information, he's asked you to confirm that you see the $600 refund he put in your account, and you say oh no I see a $6,000 refund in my account (all of this is staged) and he freaks out and begs you to do X, Y and Z to get him the $5,400 back, so he's not fired. So you start running around doing what he's asked (gift cards, Bitcoin, etc). Meanwhile you let him into your actual account which he's bleeding dry and adding insult to injury you might actually manage to buy $5,400 in gift cards give him the card number and code and you're out even more money. And boy is he grateful. When you discover the extent of the damage you are beyond devastated.
There is a variation of this that involves a phone call or email instead, calling or emailing on behalf of a grandchild, for instance, who is in need of money and of course a grandparent is going to want to help. It's always urgent enough that there is no time to call the grandchild or child to determine if there is actually an immediate danger. Getting a person frazzled is a good way to turn off the thinking part of their brain and then suggest to them how they should respond. The scammer will have very specific instructions and they will be happy to walk you through to get them the money needed... Go buy gift cards and read the information off of them, go to a Bitcoin ATM, etc. Going to the bank is less successful these days as many banks have protocols for an elderly person coming in and requesting to wire transfer a large amount of money. Bank tellers are trained to carefully ask questions to protect their customers from scams and financial loss. A simple question that they ask when it relates to a relative in mortal peril is "Oh that sounds awful what happened when you tried to reach them yourself?" So often is I didn't try, such-and-such, told me they wouldn't answer and then the banker can insist they call the person. Wise bankers have stopped untold amounts of fraud with these simple questions.
The final primary way scammers get the elderly to do what they want (they are always coming up with new ways so this is not an exhaustive list) is to verbally abuse them and demand they do certain things. This seems to be most effective on elderly women who are more likely not sure what to do when they start being demanded they do things by some stranger on the phone. Although they will employ the tactic of name calling against any woman if they think it will work. Worse because they have often done some research, or the data file on the victim already includes this information, they can use family members names and threaten to do harm to them, financial harm or release embarrassing photos, get them fired, etc, if the victim does not comply.
Considering all of these horror stories you may have gone back to considering taking away the Internet and phones to protect your family; I totally understand that. Having worked with these individuals who have been horribly scammed they might have preferred that to loosing their entire savings.
After a Scam
Mitigating damage after a scam is very time sensitive. The first problem you run into is determining what actually happened and the extent of the damage. After someone realizes they've been scammed they will likely feel embarrassed and not want to discuss exactly what happened, but exactly what happened is what must be known to prevent further damage.
If the victim let someone on their computer remotely you must assume everything on the computer has been compromised. While the scammer was working the magic of distraction it is well within possibility that everything of value on the computer was stolen - that includes all login credentials stored in browser, tax returns, Word docs that contain your passwords, other private documents and even sometimes pictures. Pictures if they found something juicy and want to use it to get additional money out of a person or in some cases it's just because they think the person / people in the pictures are attractive.
Steps to Take After a Scammer was on Your Computer
- Immediately change your banking password if you logged into your banking while they were on the remote session with you.
- Immediately change your email password if you logged into your email while they were on the remote session with you. (Update your password on your phone if you get mail there as well.)
- Notify your bank(s) and have them put a watch on your account(s). If there are already transactions that have been initiated hopefully you have contacted your bank fast enough to stop the transactions.
- Take your computer to a local computer company, like us, to have it cleaned and the remote software removed. Some banks are requiring proof of having your computer cleaned prior to re-authorizing online access to banking accounts.
- Now change every other password you had stored in your computer. This will be time consuming and laborious but unless you want to suddenly find you've lost access to your Facebook account, which is now actively selling Bitcoin to your friends, or your Amazon account suddenly starts making deliveries to people you've never heard of you'll want to get all of those passwords changed and 2FA enabled to an Authenticator App on your phone wherever possible.
This will be difficult and even more so for those who are older. If you can, accompany them with as much as possible, if a large sum of money is missing they will likely be feeling extremely overwhelmed and a family member or friend helping them remember all the steps they need to take will help them. Bear in my and remind them often if they are beating themselves up that this is a mistake that hits tens of thousands of people every year; the Internet comes with risks and professional con men who make a fortune annually by tricking people into giving them exactly what they want. Hopefully, much of the damage can be mitigated if you act quickly.


 Elderly Americans lost $12.5 billion in 2024 according to the numbers released by the
Elderly Americans lost $12.5 billion in 2024 according to the numbers released by the  Part of securing your passwords is understanding how they become compromised. Two of the most frequent ways passwords are compromised is through Brute-Force attacks and data breeches. In a Brute-Force attack, hackers are using a systematic plan to check all possibilities until the correct one is found. If a hacker knows that the site requires a minimum of 8 characters and requires the use of both alphabetical and numeric characters they will start with those parameters. This is not done by hand. They write programs to do the dirty work.
Part of securing your passwords is understanding how they become compromised. Two of the most frequent ways passwords are compromised is through Brute-Force attacks and data breeches. In a Brute-Force attack, hackers are using a systematic plan to check all possibilities until the correct one is found. If a hacker knows that the site requires a minimum of 8 characters and requires the use of both alphabetical and numeric characters they will start with those parameters. This is not done by hand. They write programs to do the dirty work. In December 2017 an amendment was made to Rule 902 Federal Rules of Evidence, specifically relating to the process for authenticating Electronically Stored Information (ESI). Until this amendment was passed, now included as subsections 13 and 14, litigants had to have any electronic evidence authenticated through trial testimony. This was an expensive process. While our company has taken on quite a bit of eDiscovery work, being asked to testify as an expert witness was rare due to the time and cost involved for litigants.
In December 2017 an amendment was made to Rule 902 Federal Rules of Evidence, specifically relating to the process for authenticating Electronically Stored Information (ESI). Until this amendment was passed, now included as subsections 13 and 14, litigants had to have any electronic evidence authenticated through trial testimony. This was an expensive process. While our company has taken on quite a bit of eDiscovery work, being asked to testify as an expert witness was rare due to the time and cost involved for litigants.